Bulletproof your network and your reputation.
Your best defense against internal and external threats is also your fast-track to cybersecurity compliance.
Created for defense contractors needing to protect sensitive technical information, the NeQter Compliance Engine is the ultimate plug-and-play solution for network-wide visibility and control, protecting proprietary information and enhancing your cybersecurity posture.
One Unified Cyber Security Suite:
A Seamless Flow of Network Information
The NeQter Compliance Engine Features:
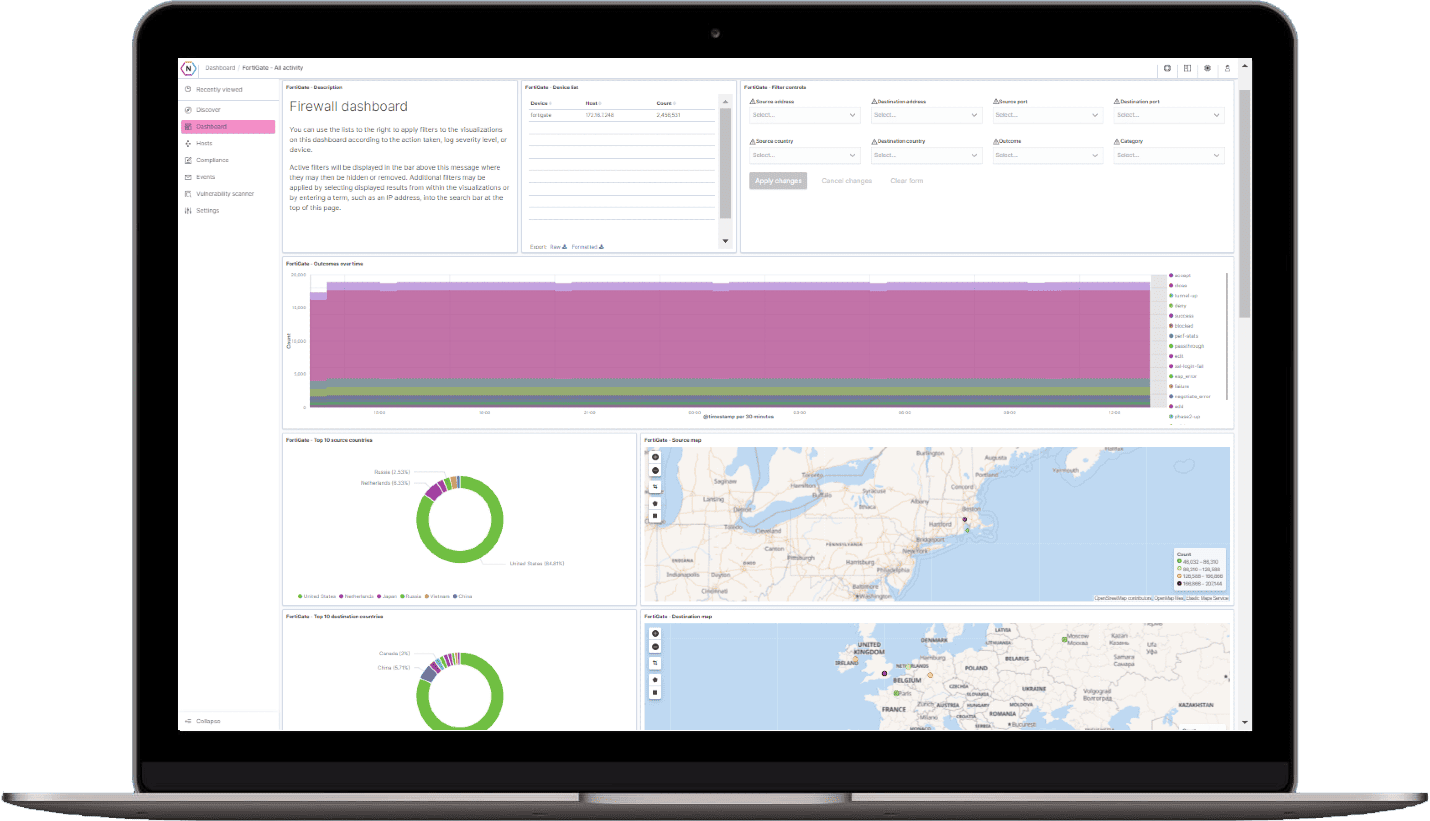
Security Information & Event Management (SIEM)
If your network is compromised, how would you know it?
Know what is going on in your network, at any given time—whether a rogue employee has malicious intent or an unassuming employee shares sensitive information or an adversary has found a loophole into your network. More importantly, turn your logs into a format that allows you to take action.
For many companies, integrating a SIEM tool, configuring data streams from all devices, parsing the data, building useful dashboards, and knowing what all of the information actually means seems overwhelming.
NeQter’s plug-and-play SIEM system features:
- Prebuilt, intuitive dashboards to visualize useful information and make it easy to interpret data, identify trends and isolate anomalies—no technical background needed
- Fully customizable alerts and notification options help you stay in tune to what is happening in your network at all times.

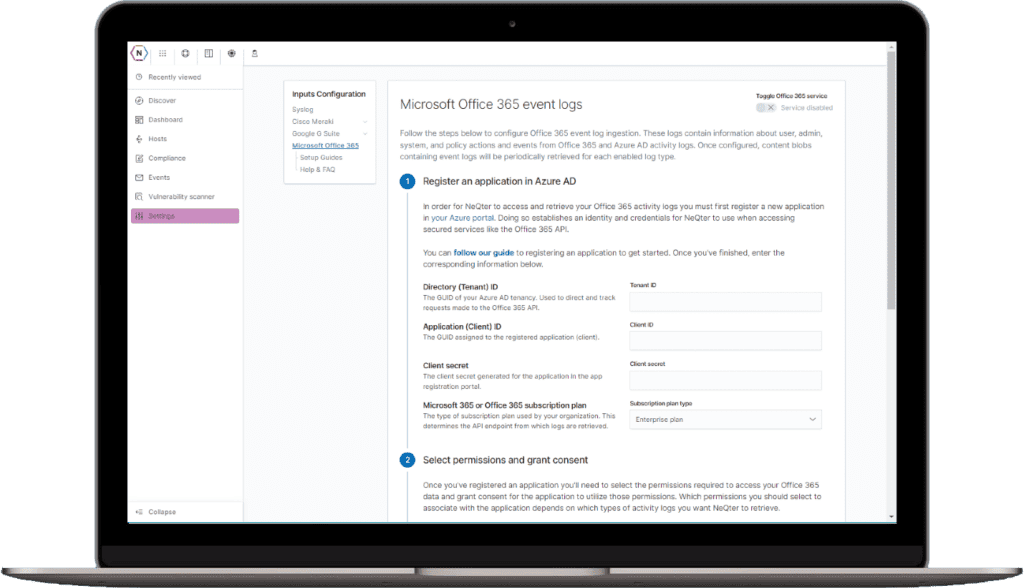
Monitoring
Out of the box integrations with all major vendors makes deployment a breeze. Begin collecting data from your all of your sources in minutes. No need to parse your own data, we have done the work for you!
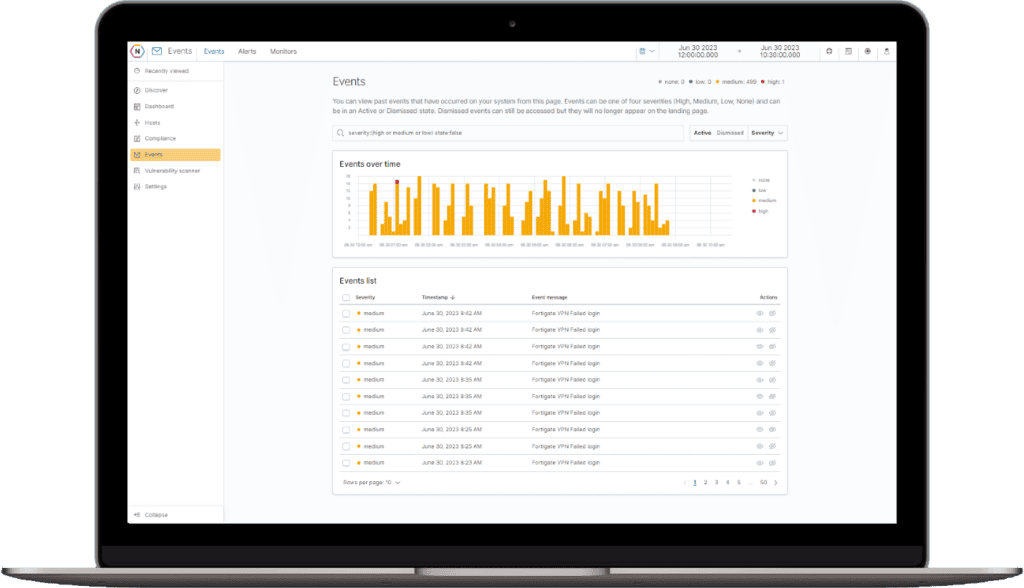
Alerting
Configure our pre-built alert templates to inform you of the most important events occurring in your environment. Want more granularity? Build your own alerts in just a few clicks!
Out-of-the-Box Integration with:















Vulnerability Detection
Find and close loopholes… before attackers find them.
Bots. Hackers. Blackhats. They surface new vulnerabilities every day, to be exploited by attackers to infiltrate your network. Most software companies deploy patches in the hopes that you’ll update your systems and stay protected. NeQter’s automated vulnerability scanning let’s you know what to fix!
NeQter’s Vulnerability Scanner features:
- Templated and fully customizable scan profiles give you the flexibility to build out processes that work for you. Want to schedule a light scan that runs weekly and a deep scan one a month? You can do that!
- NeQter taps into the latest CVE and NVT feeds, updated daily to ensure you stay up to date!
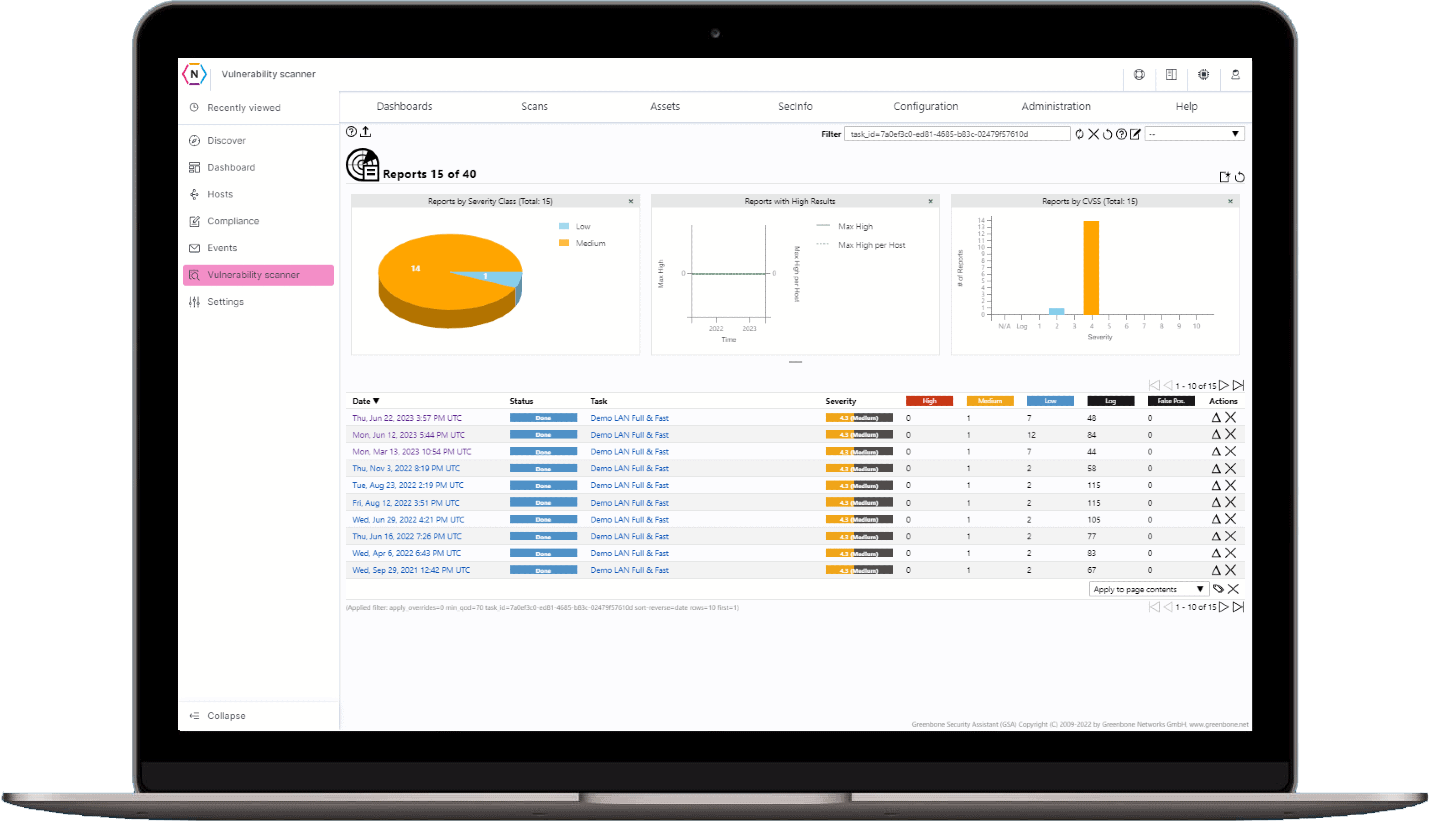

Remediation Guidance
Our vulnerability reports not only tell you what issues needs to be fixed but also how to fix them. Detailed remediation guidance, mitigations and workarounds are provided within the tool. No need to find the fix on your own!
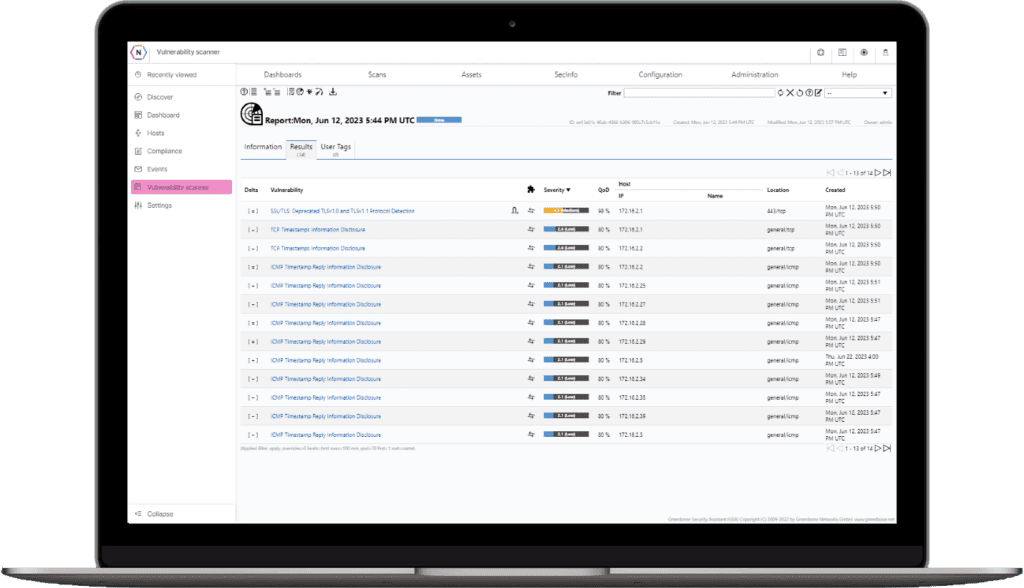
Delta Reports
Compare reports to see where you haver made progress since your last scan and where new vulnerabilities may have surfaced.
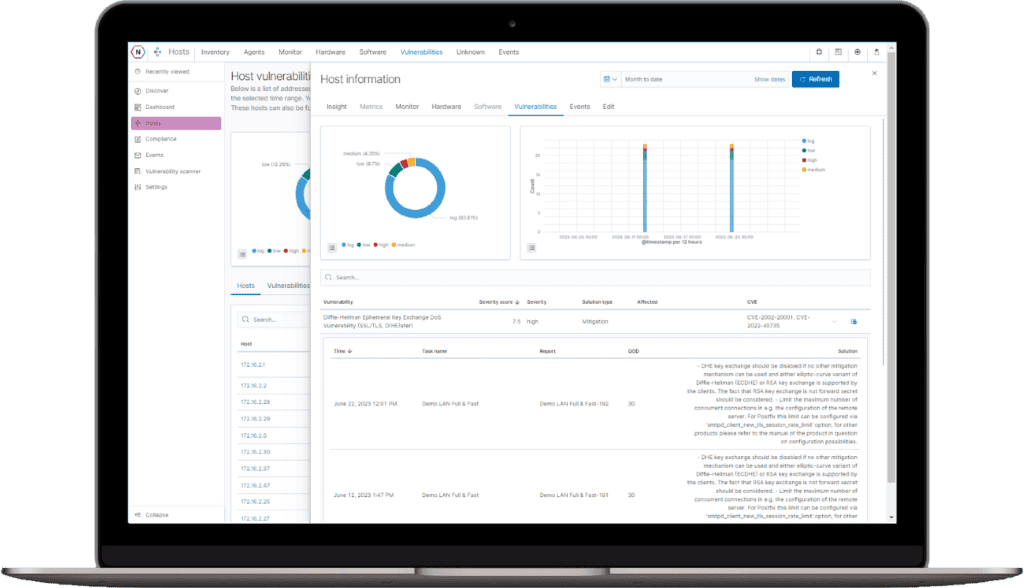
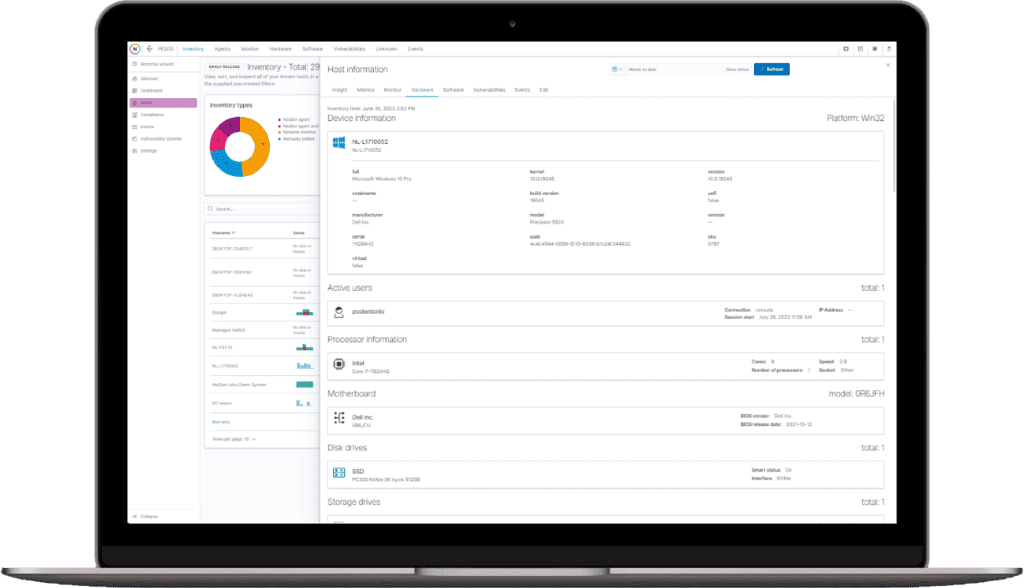
Inventory Tracking
If your network is compromised, how would you know it?
Do you know everything and everyone that’s connected to your network right now? Is it tracked in a spreadsheet? When’s the last time it was updated?
Who wants the task of updating it?
NeQter’s Inventory Tracking System features:
- Automatically audits your network for the latest inventory every 10 minutes creating an always up-to date record of hardware, software, connected devices, serial numbers, firmware and much more.
- Track and Monitor the health and status of your assets with the Host Management tool. Tag and filter your inventory with our fully customizable tagging system.
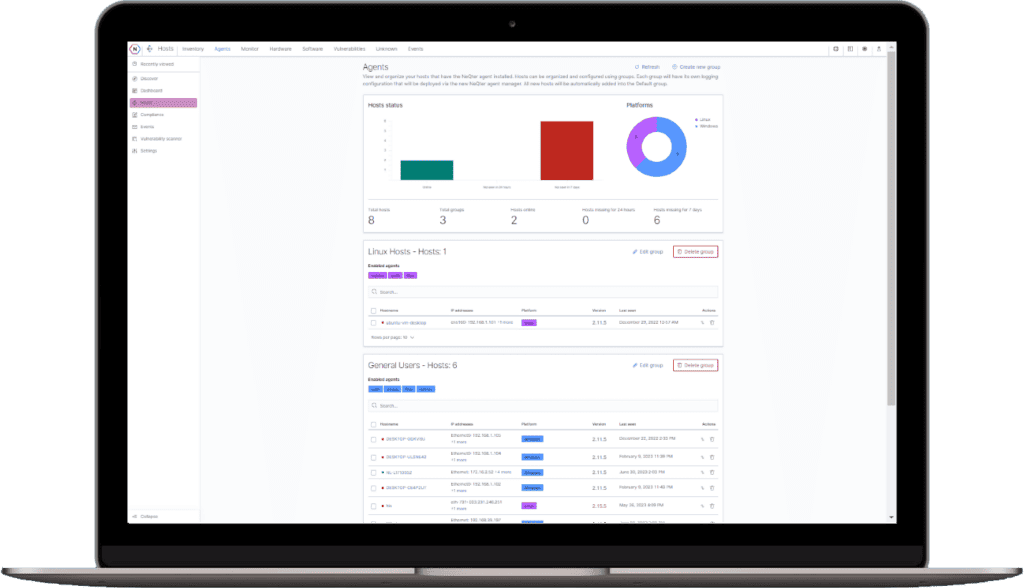
Agent Management and Groups
Deploy the NeQter Agent to collect log data and inventory metrics from your devices. Have a group of Assets that need specific logging configurations? No problem! Make a customer group, set the parameters and add your hosts to the group. It’s that easy!
Host Insight and Management
Get a global view of your hardware, software and vulnerabilities using the fully searchable Hosts Dashboards. Use the drill down capability to see the specifics of each host.
Compliance Simplified
Align Yourself with the latest standards!
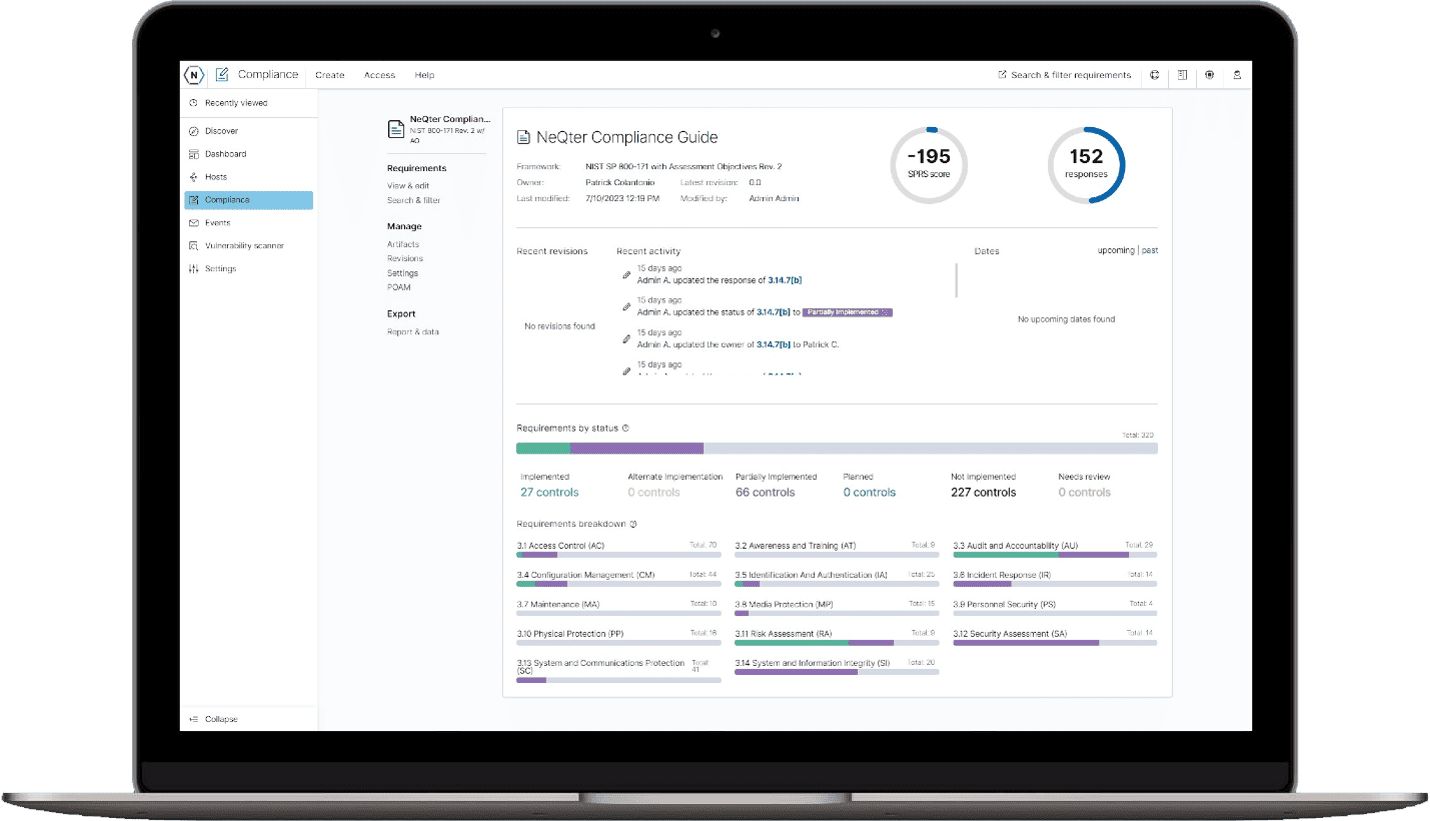
NIST SP 800-171 and CMMC are rapidly becoming the “Gold Standard” for Cybersecurity
Use the NeQter Compliance Tool to:
-
Complete Your Gap Analysis
Complete your gap analysis in a matter of hours and build your System Security Plan and POA&M in real time -
Build Your Plan
Use our prebuilt frameworks for NIST 800-171 and CMMC with granularity to the assessment objective level to produce audit ready System Security Plans.
-
Maintain your Compliance
Track your progress with intuitive dashboards and reports. Assign tasks for outstanding items and keep all of your changes logged and captured under revision control. -
Prove Your Compliance
Prove your compliance with on-demand artifact generation, real time reporting and Audit Ready Documentation.
Ready to protect your business, achieve compliance and win and retain contracts?
NeQter is the fastest, most comprehensive way to defend your business reputation, protect your customers’ proprietary information and achieve NIST SP 800-171 compliance.
Talk to us today, and let’s explore what NeQter Labs can do for your organization.